SSH tips
I’m normally a PuTTY user, but I’m temporarily on a *IX (MacOS) system, and learning a few simple techniques for doing some of what I’ve done with PuTTY, plink, and pageant. So I thought I’d jot down a few of those.
SSH keys
First, I’m using SSH keys for much of my authentication. I may add details here later on how to create those, but it’s pretty straightforward to find all over the web.
Next, ssh-add to add SSH keys to your system’s authentication agent (what PuTTY pageant does). e.g.
$ ssh-add -K /Users/breaux/my-private-key.2048.ssh
Proxy a hop
To proxy/hop through one host that can reach the other hosts you want to reach, use the ProxyCommand option. (Source of this one was fellow IBMer, Harley Stenzel.)
$ ssh -o ProxyCommand="ssh -W %h:%p my-proxy-server" my-destination-server
Further, I can tunnel ports, like the WebSphere administrator port, through that as well:
$ ssh -o ProxyCommand="ssh -W %h:%p my-proxy-server" -L9043:my-websphere-server:9043 my-destination
Where my-destination and my-websphere-server might or might not be the same server, as long as my-destination can reach my-websphere-server on the port being tunneled.
I’ll get a login shell to my-destination, and a tunneled port 9043 to my-websphere-server, through localhost:9043.
Dynamic Forwarding
Thanks, again, to Harley, this tip actually obviates some of the need for port tunneling. The -D option will dynamically forward connections through a local port, as a SOCKS server. Which… a browser can be configured to use, thus reaching any http URLs on the “other side” of that tunnel.
$ ssh -D localhost:8888 my-destination
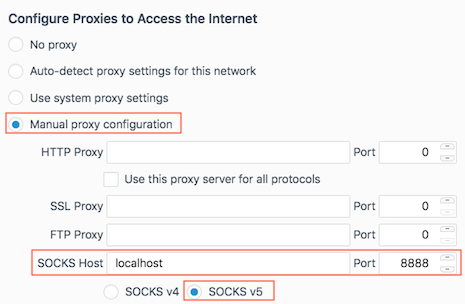
Firefox proxy settings
I’m also currently trying out the SwitchyOmega add-on to automatically switch to this proxy configuration when hitting hosts in our private domain. Thus far, it seems to be working exactly as I’d like.
Saving SSH options
Finally, .ssh/config file in your home directory can contain saved configurations. Here’s what mine looks like (again, largely thanks to Harley):
# keepalive
ServerAliveInterval 60
# proxy
host *.my.private.domain
ProxyCommand ssh -W %h:%p my-proxy-server
The first item is just to prevent our firewall from dropping my connection regularly. It sends a “keepalive” request every 60 seconds.
The second allows me to just type:
$ ssh host1.my.private.domain
and have that automatically use the configured proxy server via the ProxyCommand to connect to host1.my.private.domain. (Assuming that fully-qualified name resolves.)
You can also add Dynamic Forwarding to this file, with a line like this:
DynamicForward localhost:8888