SSH key authentication with PuTTY, Part 2, Tunneling with Plink
Following up on Part 1, here’s an additional tip which I use frequently. That is, when I need to tunnel SSH through one machine to reach others, using a background proxy with SSH key authentication for the initial connection simplifies this 2-hop process.
Automatic proxying with Plink
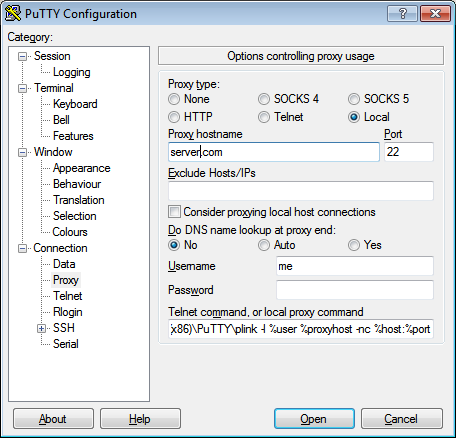
The PuTTY installation also includes a command-line SSH program called Plink which can be used in a “background” mode. The PuTTY help describes how to use Plink as a local proxy program, creating a background tunnel for the main PuTTY window. This configuration is performed in the Window > Proxy tab:
In the Proxy hostname field, you enter a host to which you have direct access and on which you’ve configured key authentication, then you refer to that host via the %proxyhost variable in the plink command you provide as the local proxy:
\path\to\plink -l %user %proxyhost -nc %host:%port
The %host and %port variables represent the ultimate destination Host Name and Port fields from the main PuTTY Session tab (which, as usual, you can enter as needed or save under separate Sessions for each server).
%user and %proxyhost are from this configuration page.
Note: If your Default Settings PuTTY profile has a username (on the Connection > Data tab) or hostname configured in it, plink will use those automatically. Discovering that wasted a couple of hours for myself and a colleague. On the other hand, if the configured default username matches your username on the proxy server, you can completely omit the -l parameter from the plink command.
Tunneling additional Ports
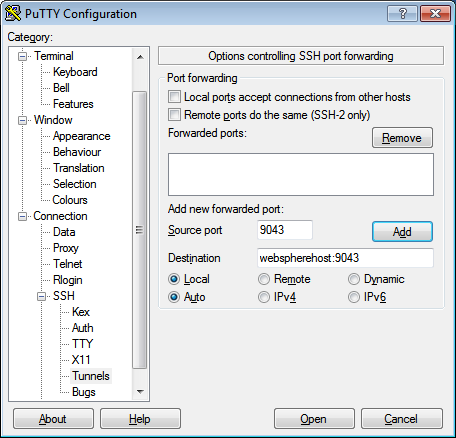
Furthermore, this technique can be used in conjunction with “normal” SSH tunneling (Connection > SSH > Tunnels) in order to tunnel a localhost port through both hops. For instance, to tunnel the default WebSphere Application Server administration console port:
Then you connect your browser to https://localhost:9043. (Don’t forget to click Add for each port you want to tunnel.)
You can similarly 2-hop tunnel X-Windows by enabling X11 Forwarding on PuTTY’s Connection > SSH > X11 tab. (You’ll need Windows X server like XMing.)
Feedback?
Any additional tips you’ve found useful? Better ways to accomplish these same tasks? I welcome your comments and suggestions.